XunRuiCMS v4.7.1 - Stored XSS via SVG File Upload
XunRuiCMS v4.7.1 - Stored XSS via SVG File Upload
Vulnerability Description
A stored Cross-Site Scripting (XSS) vulnerability has been discovered in XunRuiCMS version 4.7.1. The vulnerability exists due to insufficient validation of SVG file uploads in the dayrui/Fcms/Library/Upload.php component, allowing attackers to inject malicious JavaScript code that executes when the uploaded file is viewed.
Affected Product
- Product: XunRuiCMS
- Version: 4.7.1
- Component:
dayrui/Fcms/Library/Upload.php(File Upload Functionality) - CWE: CWE-79: Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’)
Technical Details
I built XunRuiCMS locally using the source code from GitHub. Here is the source code address:
https://github.com/dayrui/xunruicms
This is the latest XunRuiCMS v4.7.1 version, which I deployed locally using PHPStudy at http://xunrui.local/admin0d8821d43d68.php
During code analysis, I discovered that the application’s upload component (dayrui/Fcms/Library/Upload.php) allows SVG image uploads. While the system filters out the <script> tag, it does not properly sanitize other potential XSS vectors within SVG files, such as event handlers like onerror.

The vulnerability occurs because the upload validation routine only checks for explicit <script> tags but fails to validate other JavaScript execution vectors commonly found in SVG files, such as event handlers and embedded JavaScript URIs.
Proof of Concept (PoC)
The following SVG code can be used to bypass the filtering mechanism in the Upload.php component:
1 | |
Save the code above as an SVG image file:
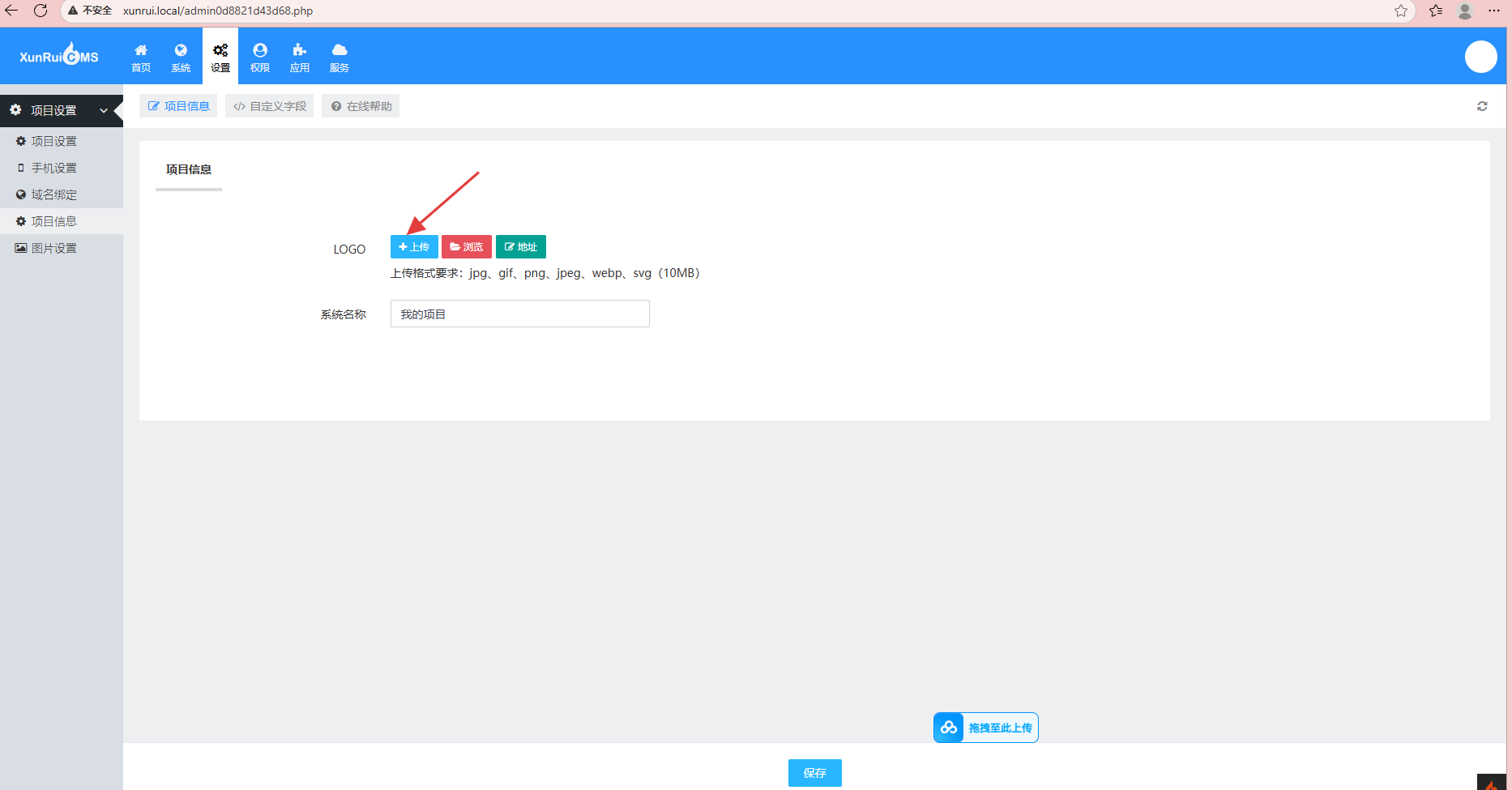
The vulnerability can be exploited through the image upload functionality:
After uploading the malicious SVG file, it is successfully stored on the server:
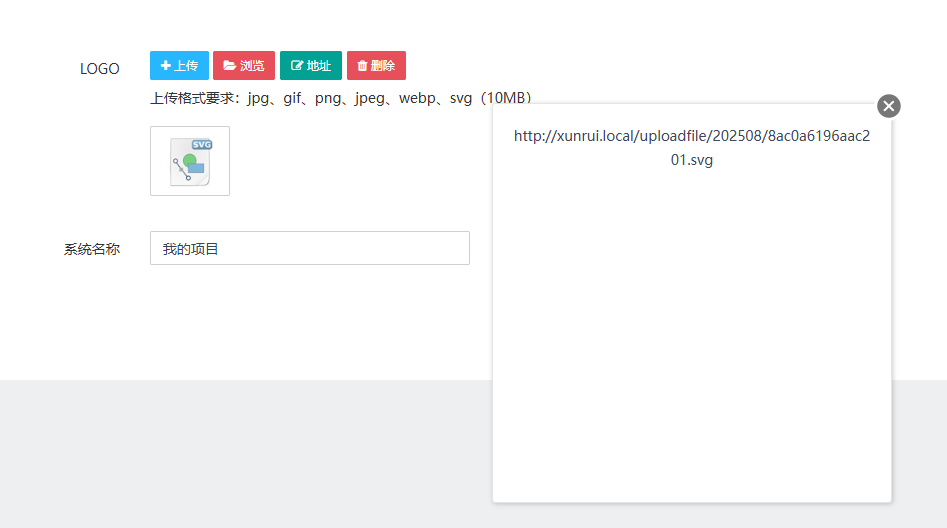
The uploaded image can also be seen in the local project:
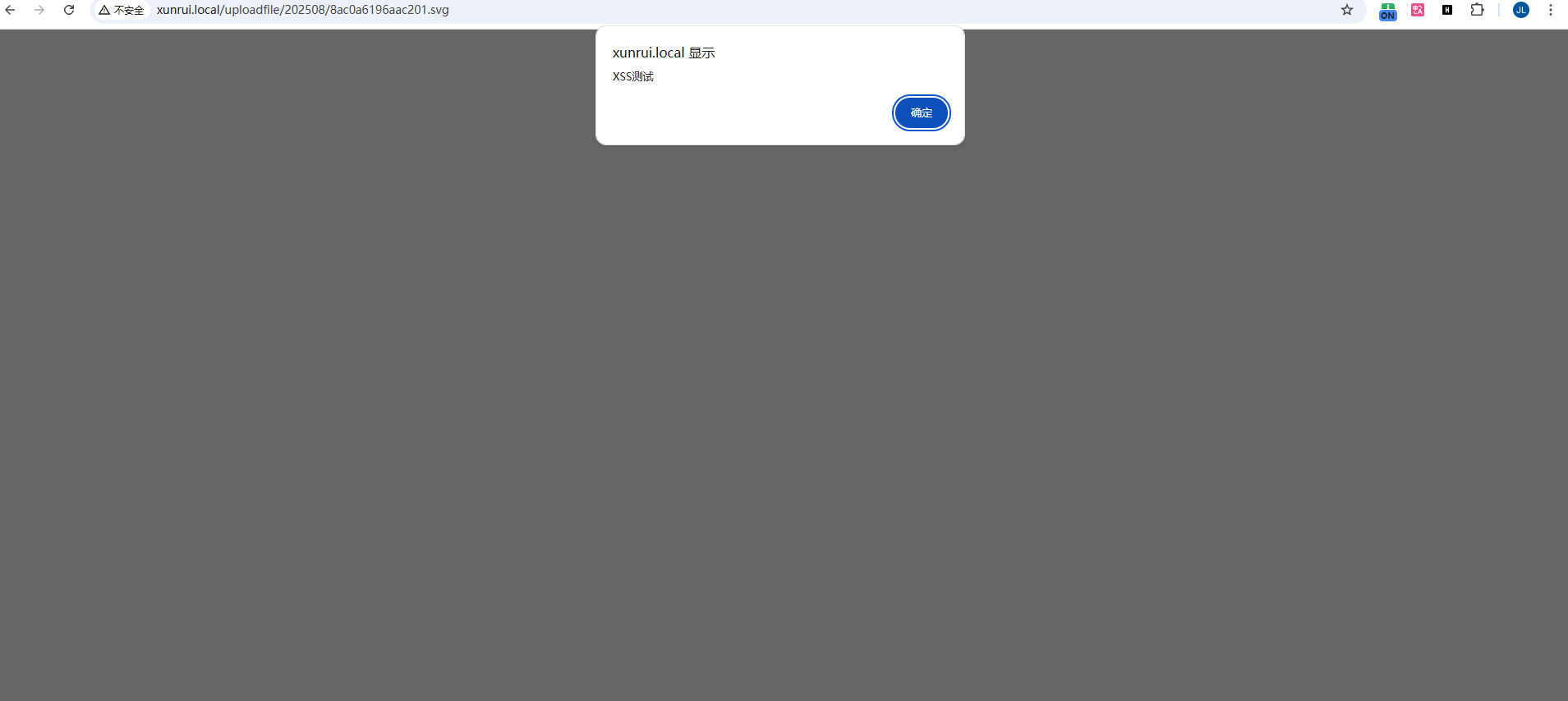
When accessing the uploaded SVG file, the JavaScript code is executed in the victim’s browser:
Impact
This vulnerability allows attackers to:
- Execute arbitrary JavaScript code in the context of other users’ browsers
- Steal sensitive information such as session cookies
- Perform actions on behalf of the victim
- Potentially escalate to more severe attacks
Vulnerable Code Analysis
The vulnerability exists in the dayrui/Fcms/Library/Upload.php component, which fails to properly sanitize SVG files before accepting them for upload. The component only checks for explicit <script> tags but does not handle other JavaScript execution vectors like event handlers (onerror, onload, etc.) that can be used within SVG elements.
Remediation
To fix this vulnerability, the application should:
- Implement proper validation and sanitization of SVG files in the
Upload.phpcomponent - Consider using a Content Security Policy (CSP) to prevent execution of inline scripts
- Convert SVG files to other image formats (like PNG) during the upload process
- Apply SVG-specific sanitization to remove potentially dangerous attributes and elements
- Update the validation routine to check for event handlers and other JavaScript execution vectors
Timeline
- 2025-08-18: Vulnerability discovered
- 2025-08-18: Documentation and proof of concept created
- [Future Date]: Vulnerability reported to vendor
- [Future Date]: CVE assigned