Information Disclosure and Source Code Leakage Vulnerability in SeaCMS
Information Disclosure and Source Code Leakage Vulnerability in SeaCMS
Vulnerability Description
A critical information disclosure vulnerability has been discovered in SeaCMS version 13.1. The vulnerability exists in the admin_safe.php component located in the /btcoan/ directory. This security flaw allows authenticated administrators to scan and download not only the application’s source code but also potentially any file accessible on the server’s root directory.
Affected Product
- Product: SeaCMS
- Version: 13.1
- Component: Security Scanning Module (
/btcoan/admin_safe.php) - CWE: CWE-200: Exposure of Sensitive Information to an Unauthorized Actor
Technical Details
I deployed SeaCMS 13.1 locally using PHPStudy with the access URL http://seacms.local/btcoan/#. The source code is available at: https://github.com/seacms-net/CMS
During security analysis of the administrative interface, I discovered that the security scanning component (admin_safe.php) intended to identify potentially vulnerable files actually exposes the full file content and allows direct download of source code files.
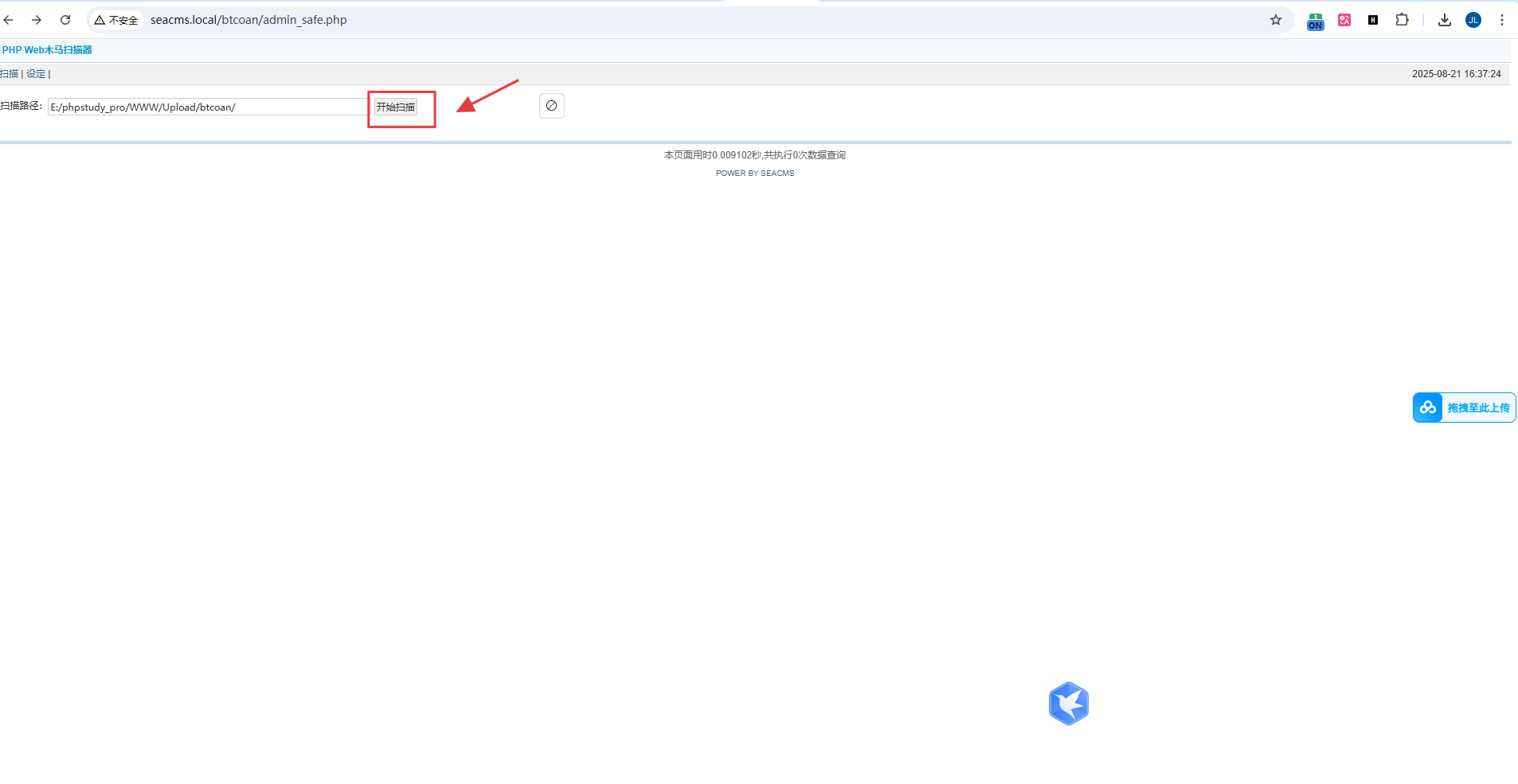
Proof of Concept (PoC)
After accessing the admin panel and navigating to the security scanning module, I clicked on “Start Scanning” and observed that the system not only identified files but also provided direct download links to their source code:
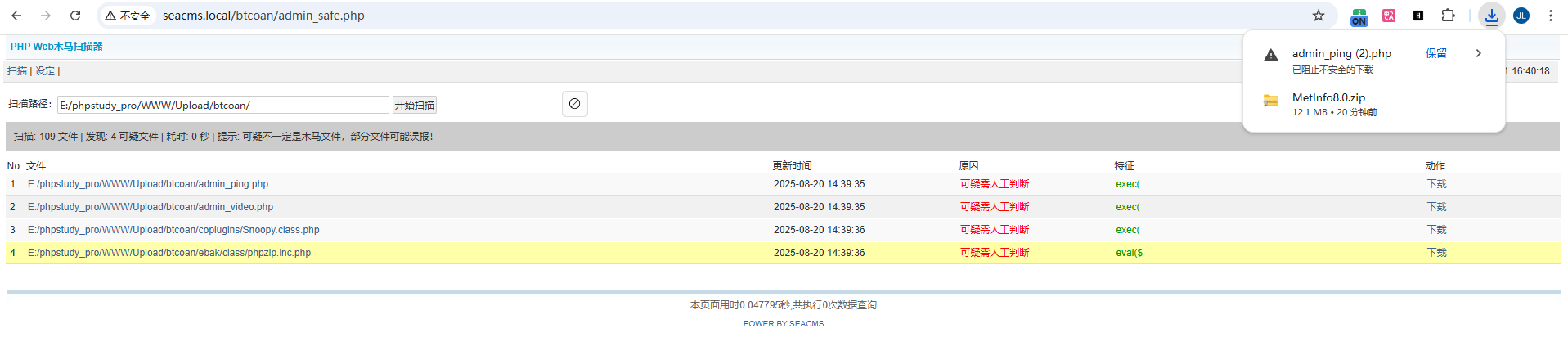
This functionality results in complete exposure of the application’s source code:
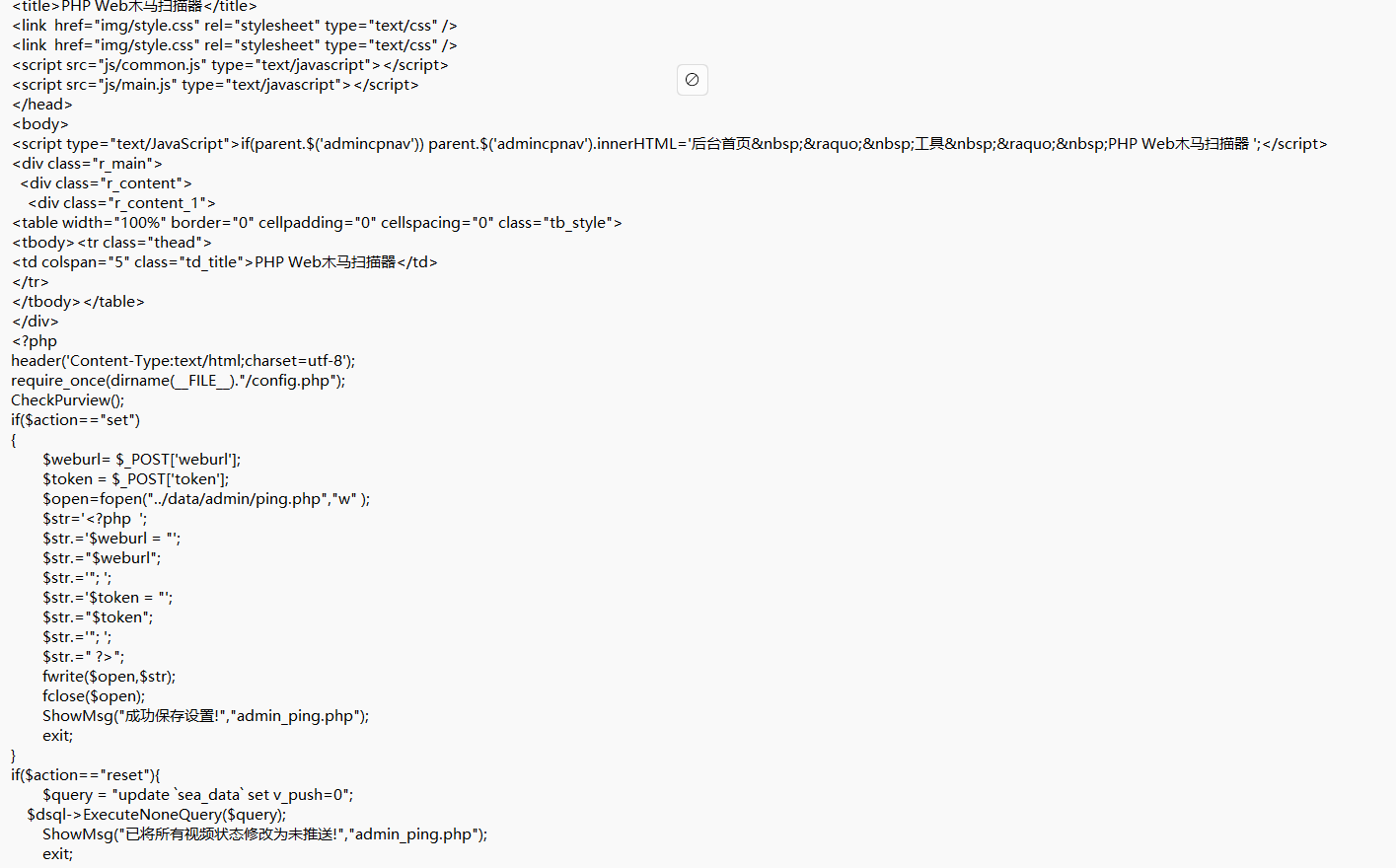
More critically, the scanning functionality is not properly confined to the application directory. It can traverse and expose files from the entire server root directory, including other applications and potentially sensitive files:
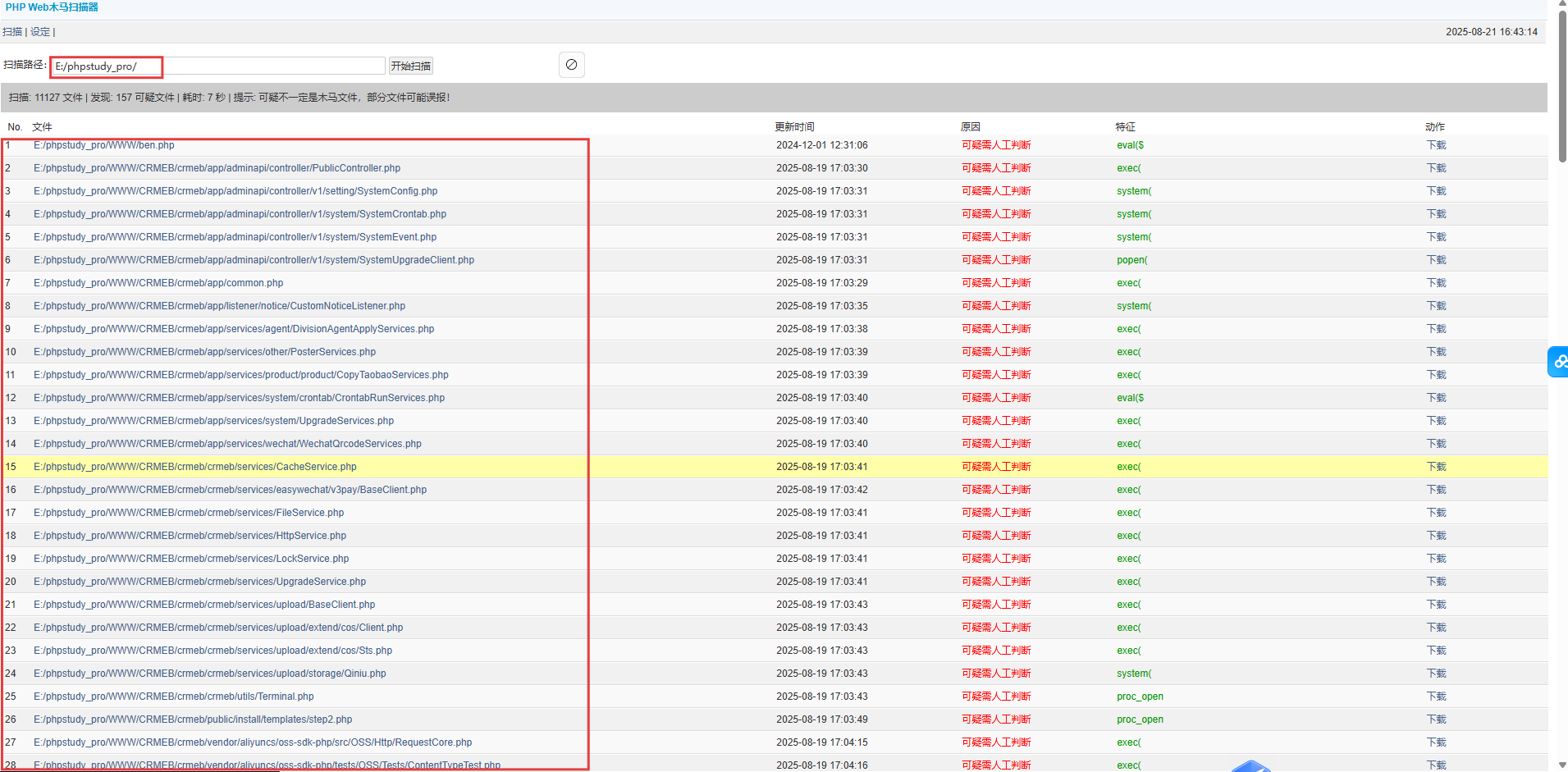
As demonstrated in the testing environment, this vulnerability allows access to all files within the PHPStudy installation directory, enabling the download of source code from any application hosted on the same server.
Vulnerable Code Analysis
The vulnerability exists in the security scanning component (admin_safe.php), which fails to:
- Properly restrict file access to the application’s directory
- Implement authorization checks for file downloads
- Sanitize file paths to prevent directory traversal
- Restrict access to sensitive application files and configurations
The core issue appears to be that the security scanning feature, intended to identify security issues, itself becomes a security liability by exposing source code and enabling unrestricted access to server files.
Impact
This vulnerability allows attackers with administrative access to:
- Download the entire application source code, exposing business logic, security mechanisms, and potential hardcoded credentials
- Access configuration files that might contain database credentials, API keys, and other sensitive information
- Access files from other applications hosted on the same server
- Gain insights that could facilitate further attacks by understanding the application’s security mechanisms
While this vulnerability requires administrative access to exploit, it represents a critical security issue as it completely compromises the confidentiality of the application’s source code and potentially exposes other sensitive server information.
Remediation
To fix this vulnerability, the application should:
- Restrict file scanning to only display metadata (file names, sizes, permissions) without providing content access
- Implement proper directory isolation to prevent access to files outside the application’s directory
- Add additional authorization checks for security scanning features
- Add logging and monitoring for sensitive administrative operations
- Consider removing or significantly restricting the file download capability from the security scanning module
Timeline
- 2025-08-21: Vulnerability discovered
- 2025-08-21: Documentation and proof of concept created
- [Future Date]: Vulnerability reported to vendor
- [Future Date]: CVE assigned