Stored XSS Vulnerability in Emlog Pro via SVG File Upload
Stored XSS Vulnerability in Emlog Pro via SVG File Upload
Vulnerability Description
A stored Cross-Site Scripting (XSS) vulnerability has been discovered in Emlog Pro 2.5.19. The vulnerability exists due to insufficient validation of SVG file uploads in the /admin/media.php component, allowing attackers to upload malicious SVG files containing JavaScript code that executes when the uploaded file is viewed.
Affected Product
- Product: Emlog Pro
- Version: 2.5.19
- Component: Media Upload Functionality (
/admin/media.php) - CWE: CWE-79: Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’)
Technical Details
I deployed the latest version of Emlog Pro 2.5.19 locally using PHPStudy. The source code is available at: https://www.emlog.net/download
During security analysis of the administrative interface, I discovered that the media upload component allows SVG files to be uploaded without proper validation or sanitization. This creates a vector for stored XSS attacks through malicious SVG content.

Proof of Concept (PoC)
After identifying the vulnerability in the media upload component, I created a malicious SVG file with the following content:
1 | |
The SVG file was successfully uploaded without any security checks:

When accessing the uploaded SVG file URL, the JavaScript code is executed in the browser context:
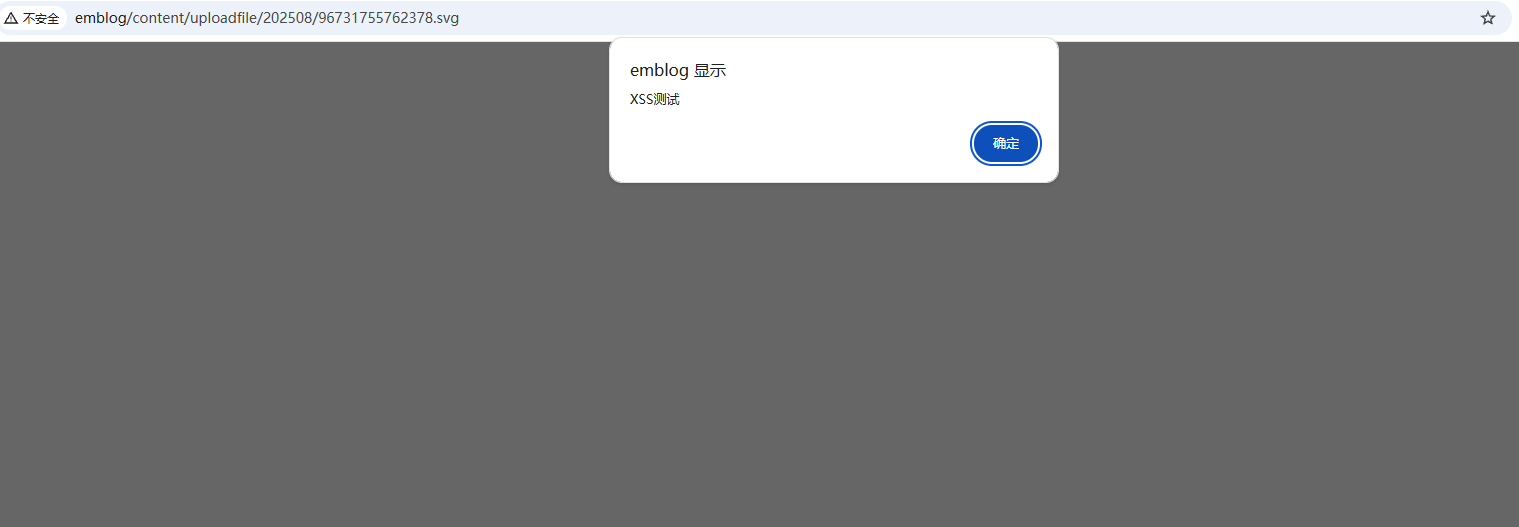
Vulnerable Code Analysis
The vulnerability exists in the media upload component, which fails to properly validate and sanitize SVG file uploads before storing them on the server. The application has several critical security issues:
- No content validation for SVG files
- No sanitization of potentially dangerous SVG elements and attributes
- SVG files are served with the correct MIME type that allows JavaScript execution
- Absence of Content Security Policy (CSP) to restrict script execution in uploaded media
Impact
This vulnerability allows attackers with administrative access to:
- Execute arbitrary JavaScript code in the context of other users’ browsers
- Steal sensitive information such as session cookies and authentication tokens
- Perform actions on behalf of the victim
- Potentially escalate to more severe attacks if combined with other vulnerabilities
While this vulnerability requires administrative access to exploit, it can be used as part of a chain attack where a lower-privileged user gains administrative access and then leverages this vulnerability to maintain persistence or escalate privileges further.
Remediation
To fix this vulnerability, the application should:
- Implement proper validation and sanitization of SVG files
- Strip potentially dangerous elements and attributes from SVG files
- Consider converting SVG files to other image formats (like PNG) during upload
- Implement a Content Security Policy (CSP) to prevent execution of inline scripts
- Serve uploaded SVG files with a MIME type that prevents script execution
Timeline
- 2025-08-21: Vulnerability discovered
- 2025-08-21: Documentation and proof of concept created
- [Future Date]: Vulnerability reported to vendor
- [Future Date]: CVE assigned