SSRF Vulnerability in MetInfo 8.0 via SVG File Upload
SSRF Vulnerability in MetInfo 8.0 via SVG File Upload
Vulnerability Description
A Server-Side Request Forgery (SSRF) vulnerability exists in MetInfo 8.0 that allows attackers to make arbitrary HTTP requests from the server by uploading malicious SVG files. The vulnerability occurs in the column management component where uploaded SVG files with embedded external image references can trigger outbound requests to attacker-controlled servers.
Affected Product
- Product: MetInfo CMS
- Version: 8.0
- Component: Column Management (
app\system\column\admin\index.class.php) - CWE: CWE-918: Server-Side Request Forgery (SSRF)
Technical Details
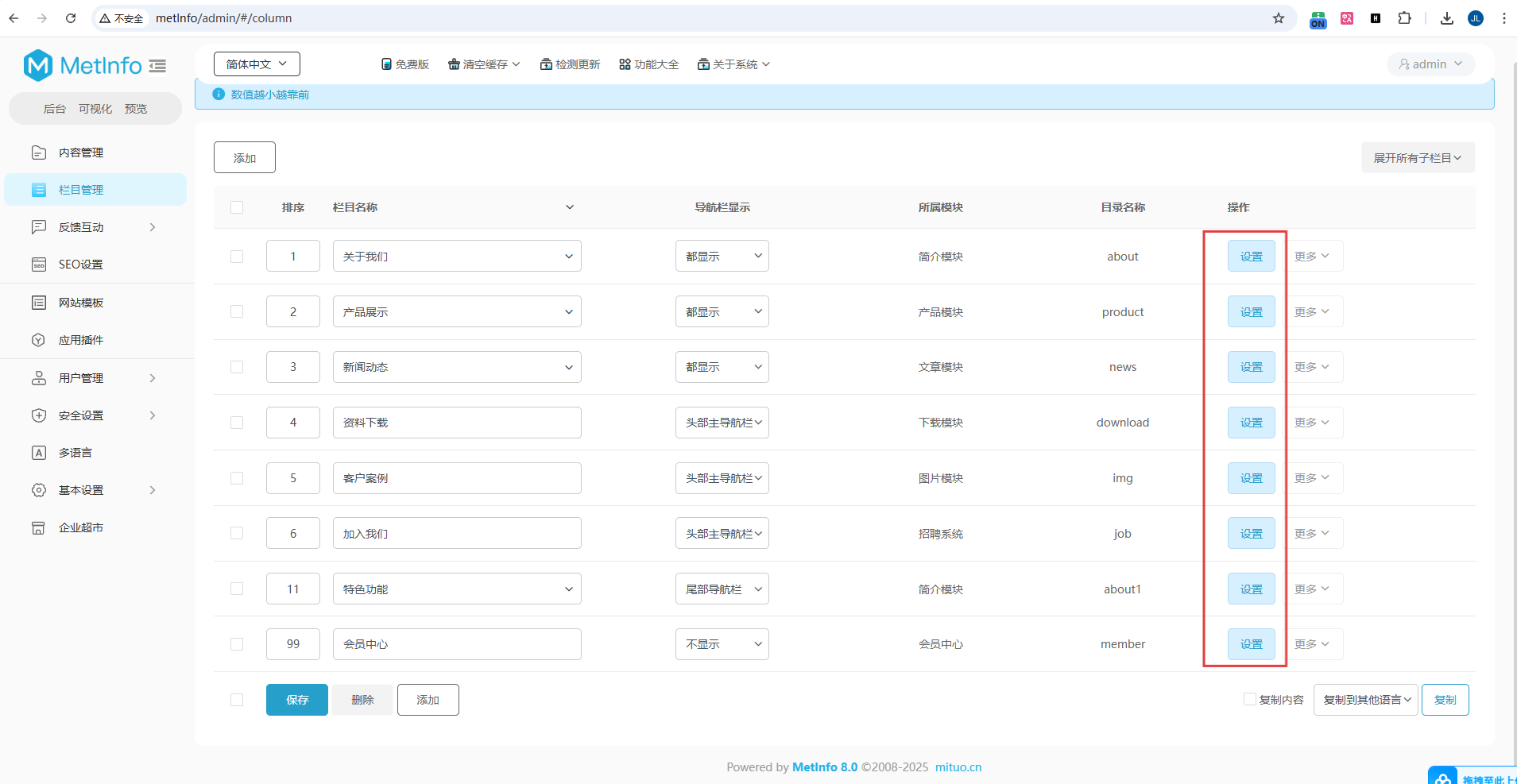
The environment was set up locally using PHPStudy, accessing the site at http://metlnfo/. After logging into the admin panel, I navigated to the column management section at http://metlnfo/admin/#/column where file upload functionality was discovered.
Column management interface:
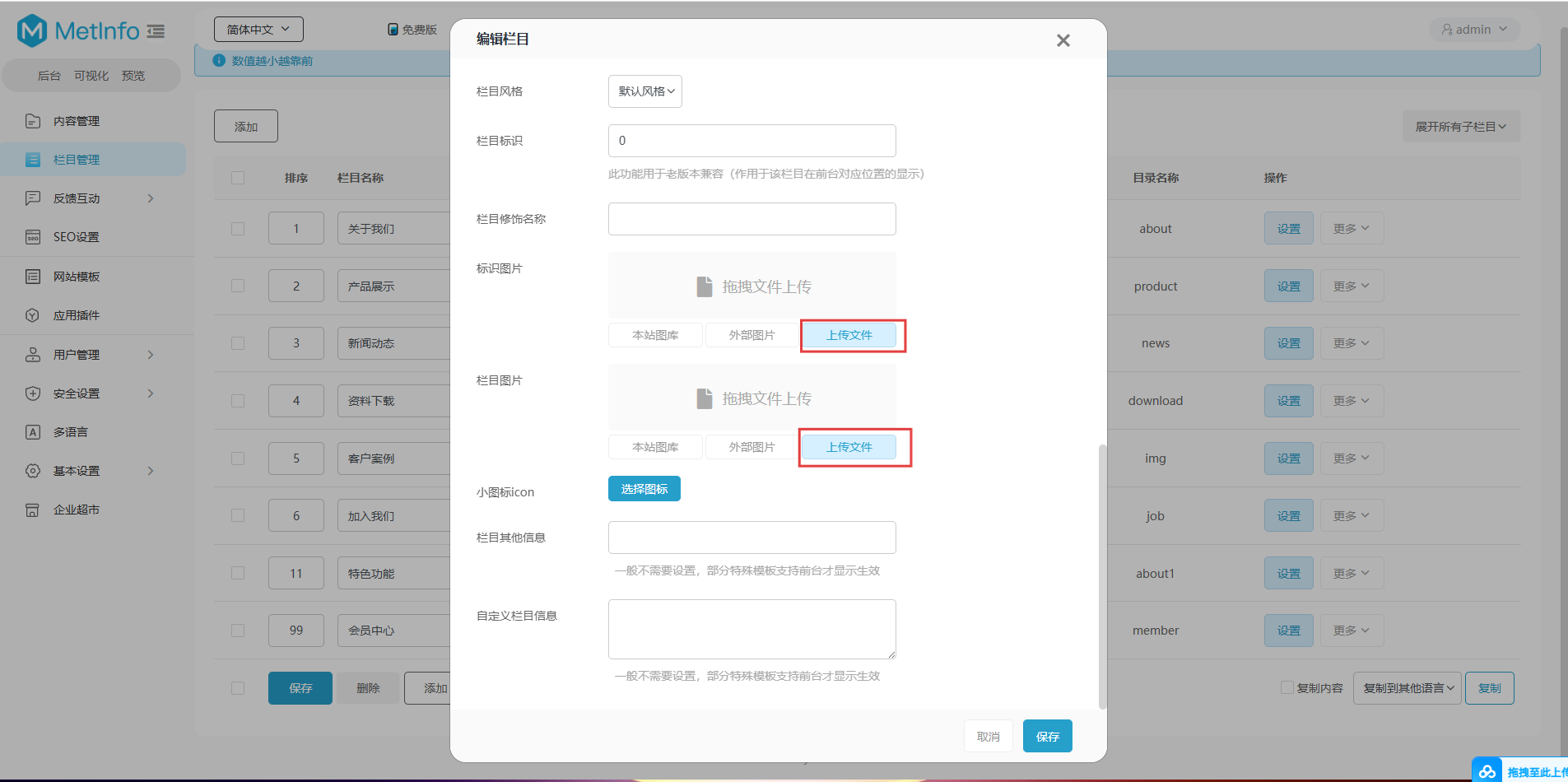
File upload functionality in settings:
Proof of Concept (PoC)
The vulnerability can be exploited by uploading an SVG file containing an external image reference that points to an attacker-controlled server. The SVG payload is as follows:
1 | |
Upload the malicious SVG file through the column management interface:
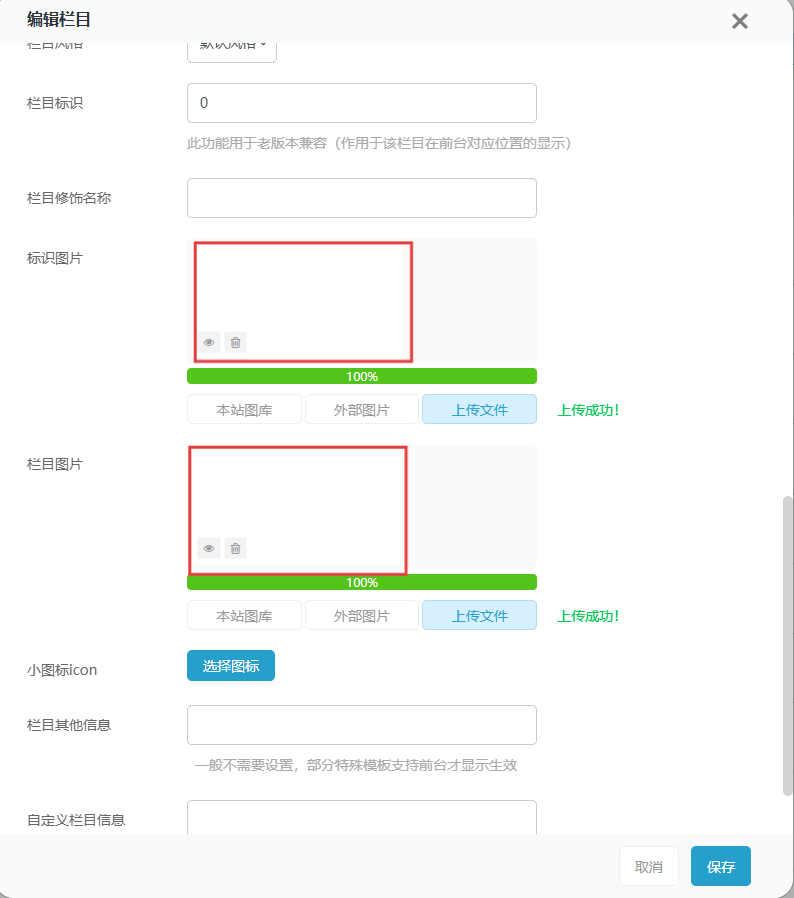
When the uploaded SVG is viewed or processed by the server, it triggers an outbound HTTP request to the specified URL:
The attacker’s server receives the request, confirming successful SSRF exploitation:
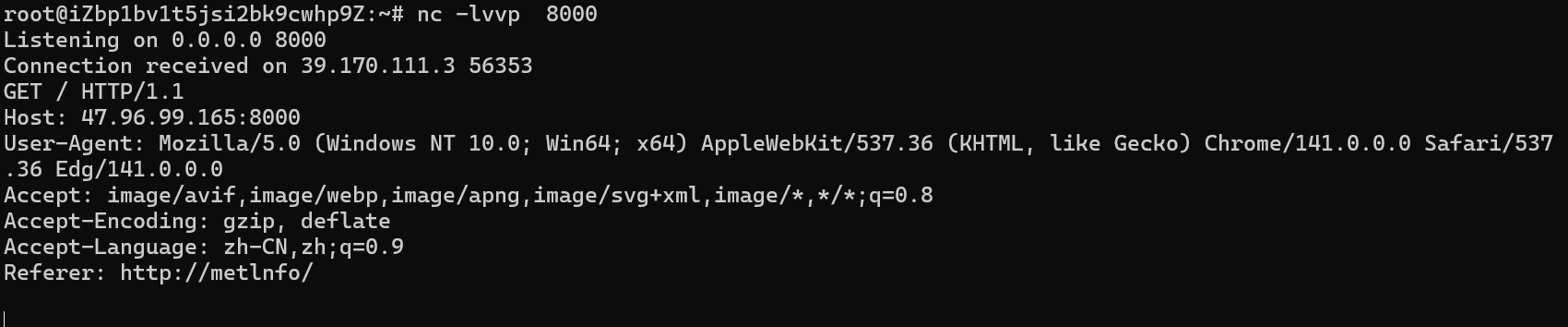
Impact
- Type: Server-Side Request Forgery (SSRF)
- Who is impacted: The MetInfo server and internal network resources
- Consequences:
- Unauthorized outbound HTTP requests from the server
- Potential access to internal services and resources
- Information disclosure through request responses
- Potential for further attacks against internal infrastructure
Remediation
To mitigate this SSRF vulnerability, MetInfo should:
- Implement strict file type validation for uploaded files
- Sanitize SVG content to remove external references before processing
- Use a whitelist of allowed domains for external resource loading
- Implement network-level restrictions to prevent outbound requests to internal networks
- Consider using a content security policy to restrict external resource loading
Timeline
- 2025-08-22: Vulnerability discovered and documented
- 2025-10-17: Additional testing and confirmation
- [Future Date]: Vendor notified
- [Future Date]: CVE requested/assigned