Stored XSS Vulnerability in MetInfo CMS Image Module
Stored XSS Vulnerability in MetInfo CMS Image Module
Vulnerability Description
A stored Cross-Site Scripting (XSS) vulnerability has been discovered in MetInfo CMS version 8.0. The vulnerability exists in the image management module, specifically in the app\system\img\admin\img_admin.class.php component. The vulnerability allows attackers to upload malicious SVG files containing JavaScript code that executes when the uploaded file is viewed or accessed by users.
Affected Product
- Product: MetInfo CMS
- Version: 8.0
- Component: Image Management Module (
app\system\img\admin\img_admin.class.php) - CWE: CWE-79: Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’)
Technical Details
I deployed MetInfo CMS 8.0 locally using PHPStudy with the access URL http://metlnfo/. The source code is available at: https://www.metinfo.cn/download/89.html
After logging into the admin panel, I accessed the image management module at http://metlnfo/admin/#/manage/?module=img&class1=130 which utilizes the vulnerable component.
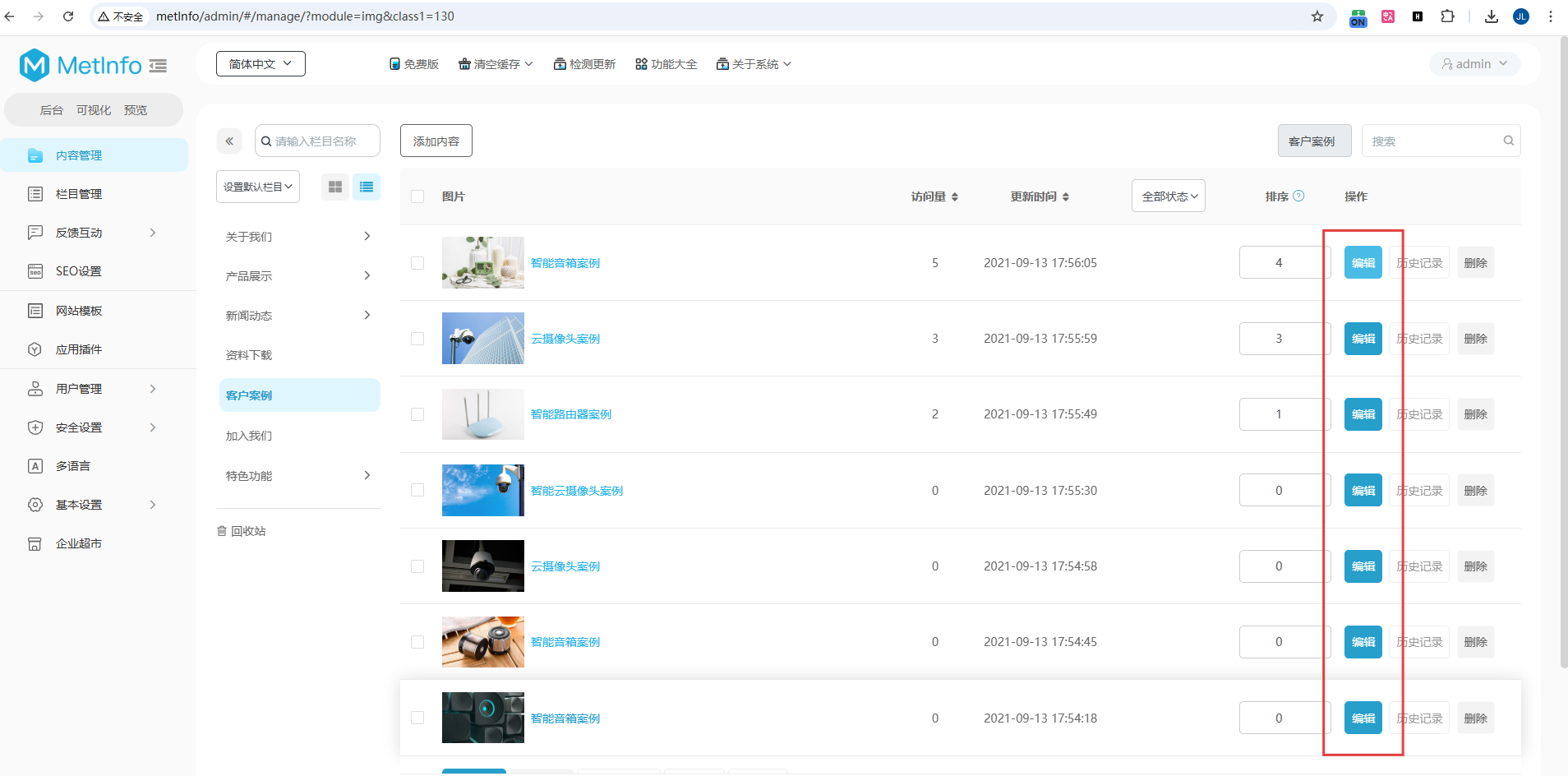
Proof of Concept (PoC)
After accessing the image management module, I selected the edit option which revealed a file upload functionality:
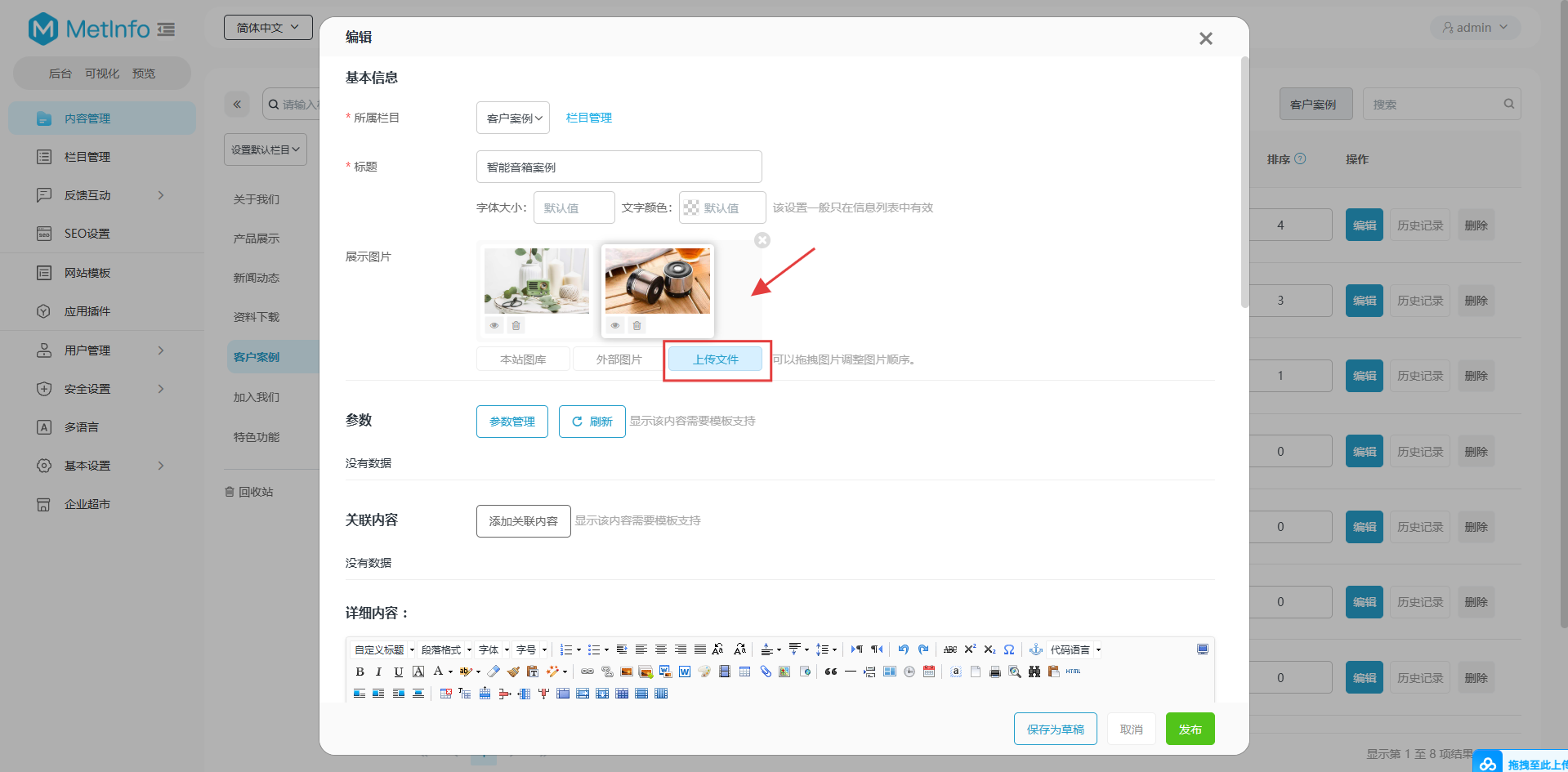
I created a malicious SVG file with the following content:
1 | |
The file was successfully uploaded without any content validation or sanitization:
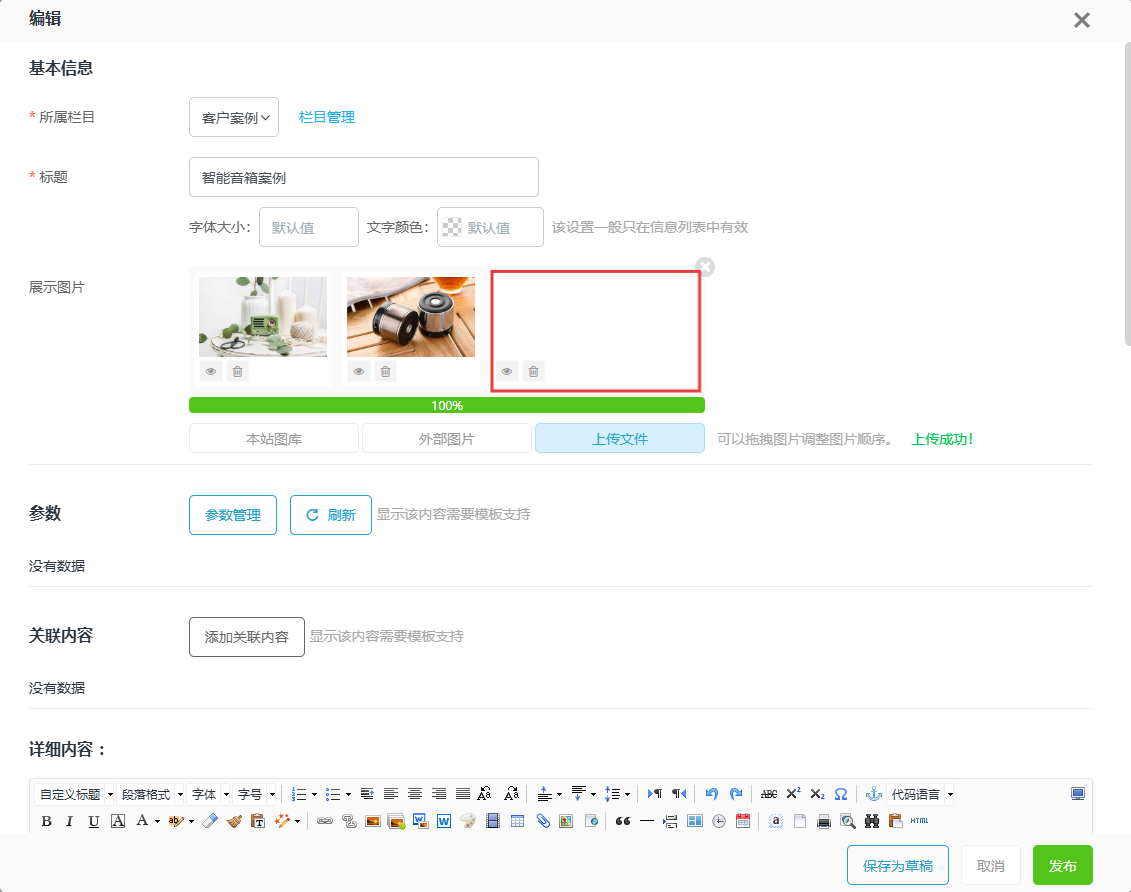
When viewing the uploaded file, the JavaScript code embedded in the SVG was automatically executed in the browser context:
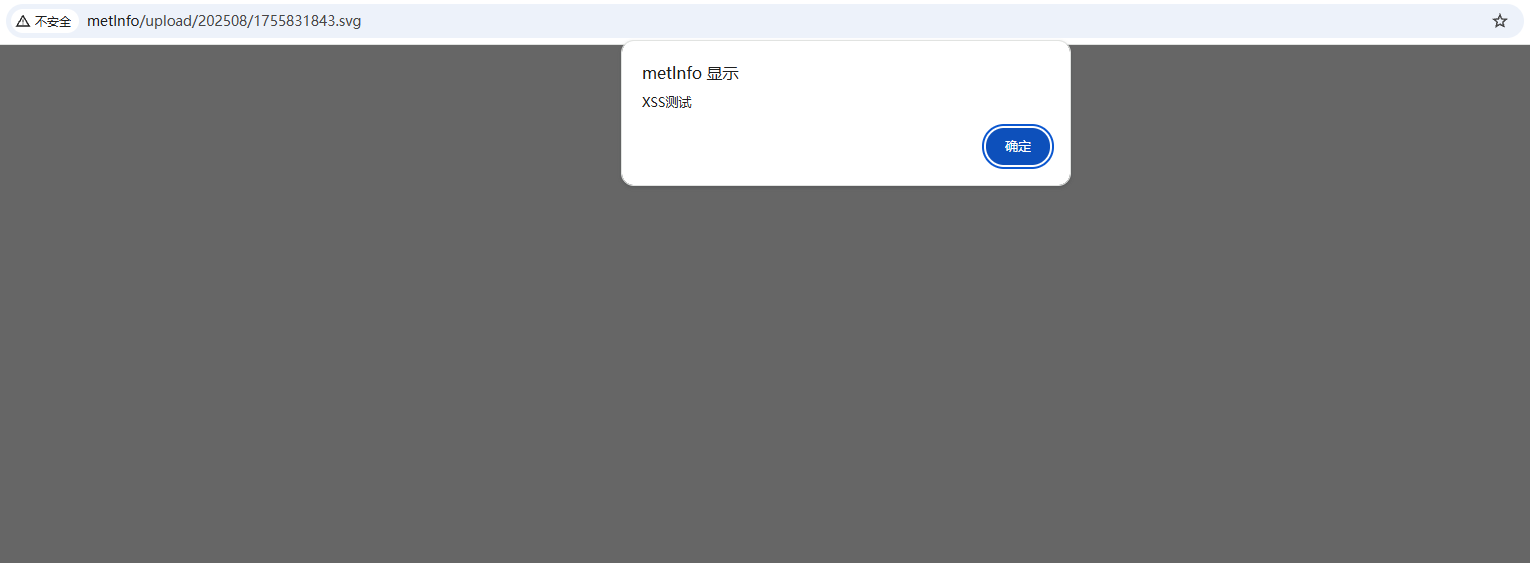
After clicking the “Save” button, the malicious SVG file was permanently stored in the system, resulting in a stored XSS vulnerability that affects both front-end users and administrators.
Vulnerable Code Analysis
The vulnerability exists in the image management module’s file upload handling, which fails to:
- Properly validate the content of SVG files before accepting them
- Sanitize potentially dangerous elements and attributes in SVG files
- Implement proper MIME type restrictions for uploaded files
- Convert SVG files to safer image formats before storing them
The core issue is that the image management module allows SVG files to be uploaded and later served with the correct MIME type that enables JavaScript execution within the browser.
Impact
This vulnerability allows attackers with administrative access to:
- Execute arbitrary JavaScript code in the context of other users’ browsers, including administrators and front-end users
- Steal sensitive information such as session cookies and authentication tokens
- Perform unauthorized actions on behalf of victims
- Potentially escalate to more severe attacks by chaining with other vulnerabilities
As confirmed in testing, the impact extends to both front-end and back-end users, creating a significant security risk for all site visitors.
Remediation
To fix this vulnerability, the application should implement the following security measures:
- Enhance the image management module to perform content validation and sanitization of SVG files
- Strip potentially dangerous elements and attributes from SVG files
- Consider converting SVG files to raster image formats (PNG, JPEG) during the upload process
- Implement proper Content Security Policy (CSP) headers to prevent script execution from uploaded files
- Serve SVG files with a MIME type that prevents script execution (e.g.,
image/svg+xml-sanitized)
Timeline
- 2025-08-22: Vulnerability discovered
- 2025-08-22: Documentation and proof of concept created
- [Future Date]: Vulnerability reported to vendor
- [Future Date]: CVE assigned